CentOS7上使用strongSwan搭建IPsec __VPN服务
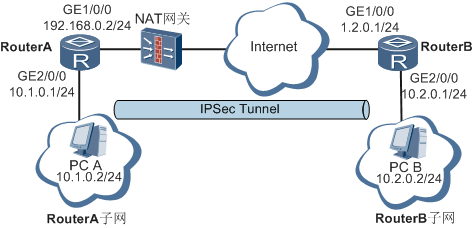
公司使用电信私有云服务,服务器在电信私有云平台,不支持vpn产品,需要自行搭建vpn站点,公司内部使用华为usg防火墙做为vpn网关。为解决公司到云平台网络互通,故决定使用ipsec搭建站点到站点vpn隧道。
服务器公网IP要作为我们的网关,需要将服务器开启转发:
加入此行 net.ipv4.ip_forward = 1
利用iptables 实现nat MASQUERADE 共享上网
1、安装strongSwan,可以使用源码安装,但此次我们主要针对配置相关讲解,故使用yum安装
2、查看strongSwan版本,命令和结果如下:
3、安装完成先配置ipsec.conf文件。
以下是真实的配置文件:
4、配置ipsec.secrets文件。
配置文件如下:PSK需要是大写,冒号前后需要有空格,密码需要有双引号
5、配置 sysctl.conf文件
配置文件如下:
使配置生效:
6、启动服务:
IPSec监听在UDP的500和4500两个端口,其中500是用来IKE密钥交换协商,4500是nat穿透的。
7、设置开机自动启动
8、运行strongswan status,查看IPsec 状态已经建立。
9、运行ip xfrm policy,查看路由策略。可以看到路由已建立。
StrongSwan 搭建IPsec (IKEv1 and IKEv2) 实现不同局域网之间通讯
使用strongswan搭建属于你自己的私有IPsec (IKEv1 IKEv2)
一、 环境和前期准备工作
1. 环境
2. 配置环境
br /
二、 搭建步骤
注意事项: 安装后一定要做软连接,并且清楚自己的虚拟化方案是哪个,加入正确的配置,否者会照成无法上网
注意事项 : 服务器这边的CN一定是你网卡的ip,或者你网卡ip对应的域名,–san 设置设置别名,建议设置两个或者两个以上,分别为你的域名和网卡ip;–flag serverAuth 表示证书使用用途,不加windows 7会报错,非 iOS 的 Mac OS X 要求了“IP 安全网络密钥互换居间(IP Security IKE Intermediate)”这种增强型密钥用法(EKU),–flag ikdeIntermediate;
vim /usr/local/strongswan/etc/ipsec.conf
vim /usr/local/strongswan/etc/strongswan.conf
2.编辑 /etc/systcl.conf
3.开启 firewall的转发功能
三、 各种终端测试
strongswan 配置文件 /etc/ipsec.conf 速查手册1
英文文档:
what operation, if any, should be done automatically at IPsec startup.
auto= add loads a connection without starting it.
auto= route loads a connection and installs kernel traps. If traffic is detected between leftsubnet and rightsubnet, a connection is established.
auto= start loads a connection and brings it up immediately.
auto= ignore ignores the connection. This is equal to deleting a connection from the config file. Relevant only locally, other end need not agree on it.
comma-separated list of ESP encryption/authentication algorithms to be used for the connection, e.g:
The notation is encryption-integrity[-dhgroup][-esnmode] .
For IKEv2, multiple algorithms (separated by -) of the same type can be included in a single proposal.
IKEv1 only includes the first algorithm in a proposal. Only either the ah or the esp keyword may be used, AH+ESP bundles are not supported.
Defaults to aes128-sha256 ( aes128-sha1, 3des-sha1 before 5.4.0 ). The daemon adds its extensive default proposal to this default or the configured value. To restrict it to the configured proposal an exclamation mark ( ! ) can be added at the end.
Note:
As a responder, the daemon defaults to selecting the first configured proposal that’s also supported by the peer. By disabling charon.prefer_configured_proposals in strongswan.conf this may be changed to selecting the first acceptable proposal sent by the peer instead.
In order to restrict a responder to only accept specific cipher suites, the strict flag ( ! , exclamation mark) can be used, e.g:
If dh-group is specified, CHILD_SA rekeying and initial negotiation include a separate Diffe-Hellman exchange (since 5.0.0 this also applies to IKEv1 Quick Mode). However, for IKEv2, the keys of the CHILD_SA created implicitly with the IKE_SA will always be derived from the IKE_SA’s key material. So any DH group specified here will only apply when the CHILD_SA is later rekeyed or is created with a separate CREATE_CHILD_SA exchange. Therefore, a proposal mismatch might not immediately be noticed when the SA is established, but may later cause rekeying to fail.
Valid values for esnmode are esn and noesn . Specifying both negotiates extended sequence number support with the peer, the default is noesn .
Refer to IKEv1CipherSuites and IKEv2CipherSuites for a list of valid keywords.
encryption-integrity[-dhgroup][-esnmode]
对称加密算法-校验算法[-会话密钥交换算法][-有无ESN模式]
参见
comma-separated list of IKE/ISAKMP SA encryption/authentication algorithms to be used, e.g:
The notation is encryption-integrity[-prf]-dhgroup . In IKEv2, multiple algorithms and proposals may be included, such as aes128-aes256-sha1-modp3072-modp2048,3des-sha1-md5-modp1024 .
The ability to configure a PRF algorithm different to that defined for integrity protection was added with 5.0.2 .
If no PRF is configured, the algorithms defined for integrity are proposed as PRF. The prf keywords are the same as the integrity algorithms, but have a prf prefix (such as prfsha1 , prfsha256 or prfaesxcbc ).
Defaults to:
( aes128-sha1-modp2048,3des-sha1-modp1536 before 5.4.0 ) for IKEv1.
The daemon adds its extensive default proposal to this default or the configured value. To restrict it to the configured proposal an exclamation mark ( ! ) can be added at the end.

Refer to IKEv1CipherSuites and IKEv2CipherSuites for a list of valid keywords.
Note : As a responder both daemons accept the first supported proposal received from the peer. In order
to restrict a responder to only accept specific cipher suites, the strict flag ( ! , exclamation mark)
can be used, e.g:
encryption-integrity[-prf]-dhgroup
对称加密算法-校验算法[-prf]-会话密钥交换算法
参见
参考文档:
感谢您的来访,获取更多精彩文章请收藏本站。




















![表情[woshou]-国际网络专线](https://urenkz.com/wp-content/themes/zibll/img/smilies/woshou.gif)
![表情[yangtuo]-国际网络专线](https://urenkz.com/wp-content/themes/zibll/img/smilies/yangtuo.gif)
![表情[xiaoyanger]-国际网络专线](https://urenkz.com/wp-content/themes/zibll/img/smilies/xiaoyanger.gif)




暂无评论内容